Some events in life are making me reconsider what physical possessions I lug around in life. I’ve pondered what would make me get rid of something. A new thought has been rattling around in my head today: “Why do I own that item?”
There are some obvious answers, such as you own clothes to be publicly discrete and conform socially. You own a car to commute to work, so you can earn money to fund the rest of life.
Okay. Why the second car? Well, for me, I tend to own older cars, so maybe it’s to provide backup or reliability in case one is out of service. If that is the reason, then the economic cost to compare with is renting a car instead. Pushed into the corner, I think renting would be cheaper since cars breaking down is more a fear than a reality for me.
Or, maybe there’s a mission need for another vehicle. For example, you purchase a truck to augment your car because it tows your tailer. I know it seems sterile and offensive, but consider the cost of whatever you’re trailering. If it’s a boat, the cost of operating that boat just went way up when you factor in the truck. ..if that’s the real reason you bought the truck.
I’m a system engineer. I think it would be instructive to draw a causal tree diagram, and force myself to consider what possessions I have for their own primary use, and what ones are second layer items. I have a suspicion that I’ll own fewer things if I actually figure this all out and let numerical comparisons drive my decisions.
- Why do I own the 17th dress shirt?
- Why do I own that mantle-piece decoration?
- Why do I own a second vacuum cleaner?
- Why do I own the second pair of boots?
- Why own blankets and sheets vs a single sleeping bag?
To bracket the problem, here is one extreme to consider: Yes, I’ll keep the hand drill. It’s cheap enough and ownership burdens are few enough that it’s just not worth calling in the repairman to drill a hole. I purchased a $9.34 drill bit last month. Still a lot cheaper than alternatives.
On the other extreme is the house trailer I owned. Considering gas mileage for the tow vehicle, insurance, licensing, etc., I calculated that if I drove more than 520 miles a day while vacationing with the trailer, it was a money looser compared to renting hotel rooms. In otherwords, it’s cheap to park and use it. But it’s not cheap to go cross-country with it. Most of my trips are the cross-country type. I owned it for emotional fantasy reasons that were’t real, so I sold it.

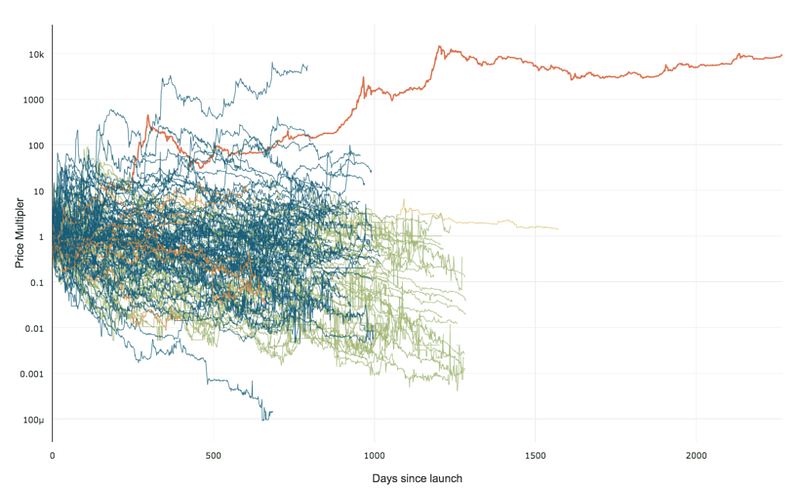 99% of ICOs Will Fail
99% of ICOs Will Fail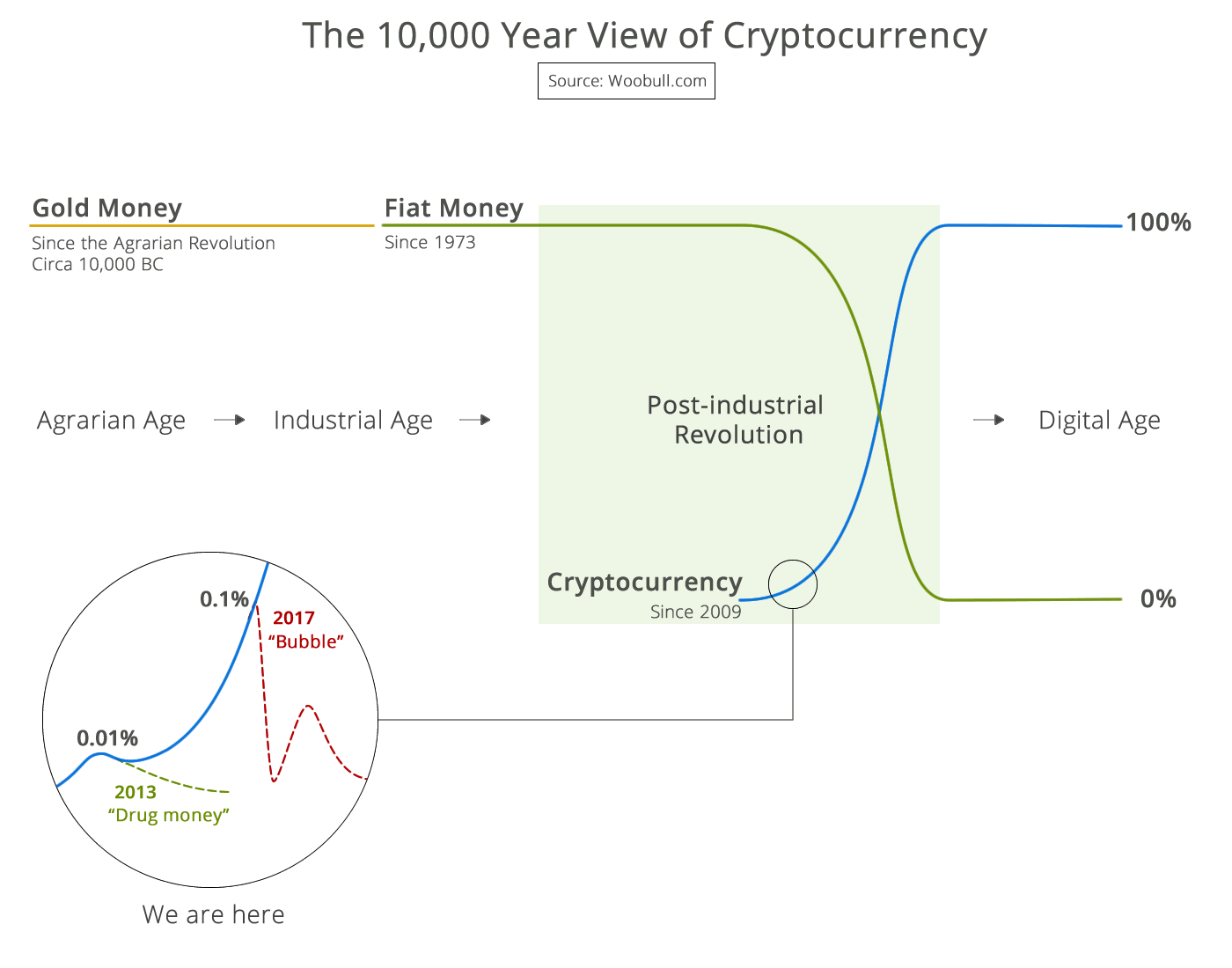 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency