So imagine yourself a spy, trying to break a secret code. After you decode the message, how do you know if you did it correctly?
Most people think, “Oh, well if it makes a readable sentence, I have done it correctly.” But what if that method fails? If there is no way to know, it is impossible to decode the message. I don’t mean computationally difficult. I mean impossible. This is the purity of One-Time-Pad encryption.
With the English language, there are many sentences that can exist and communicate something. A OTP encrypted message can be turned into any one of them based on what key you select. This creates an interesting idea of creating two different outcomes using two different keys. I have a demonstration of this in a prior blog entry.
code + key1 -> “you’re nice”
code + key2 -> “you’re mean”
I fantasize about writing a will that is handed to all my beneficiaries upon my death. Much earlier (even now) I give them individualized keys. When combined with my will, each person gets a customized document indicating their inheritence. Cool, isn’t it? No document stands alone. Only when they come together are they be purposeful.
There is a certain symmetry of the code and the key. I could say that two individuals were given different keys. Equivalently truthful would be the statement that I gave them different codes with the same key. It’s an arbitrary word definition.
key + code1 -> “you’re nice”
key + code2 -> you’re mean”
Leaving English sentences and documents behind, allow me to substitute the idea of sentences with “secondary encryption key.” Can OTP be used to encrypt a secondary key perfectly? Maybe the insanely long key to decrypt my hard drive can be stored with a simple OTP encryption.
I think OTP cannot be used to encrypt a secondary key becuase there are not an infinite supply of secondary keys that can exist and communicate something. Therefore, it is only computationally difficult to break the encryption, rather than theoretically impossible. Each secondary key you get, you could try to decode the disk drive with it and it would be obvious that most of them did not work. It’s not like an English sentence, where they all make sense.
One last thought. I have found a program that lets me specify the before-document and the after-document and generate the key that converts from one to the other. I want to find or create a program that reads two separate image files and calculates the OTP image key that converts from one image to the other. I’ll call the program “Dorian Gray” 🙂

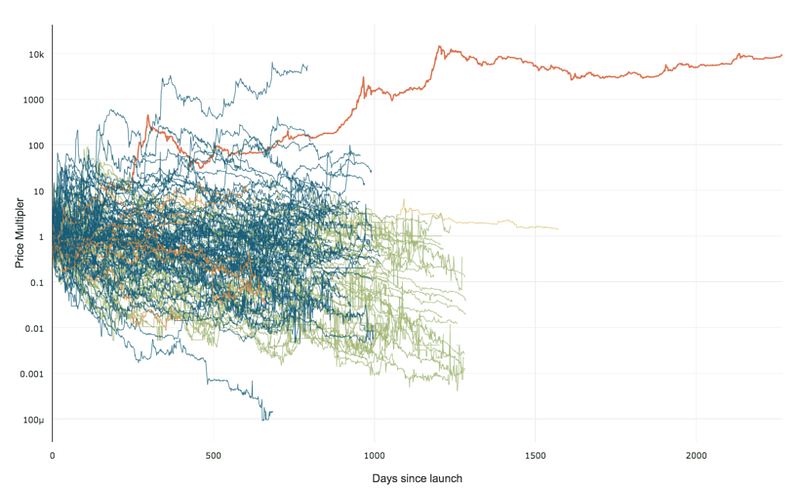 99% of ICOs Will Fail
99% of ICOs Will Fail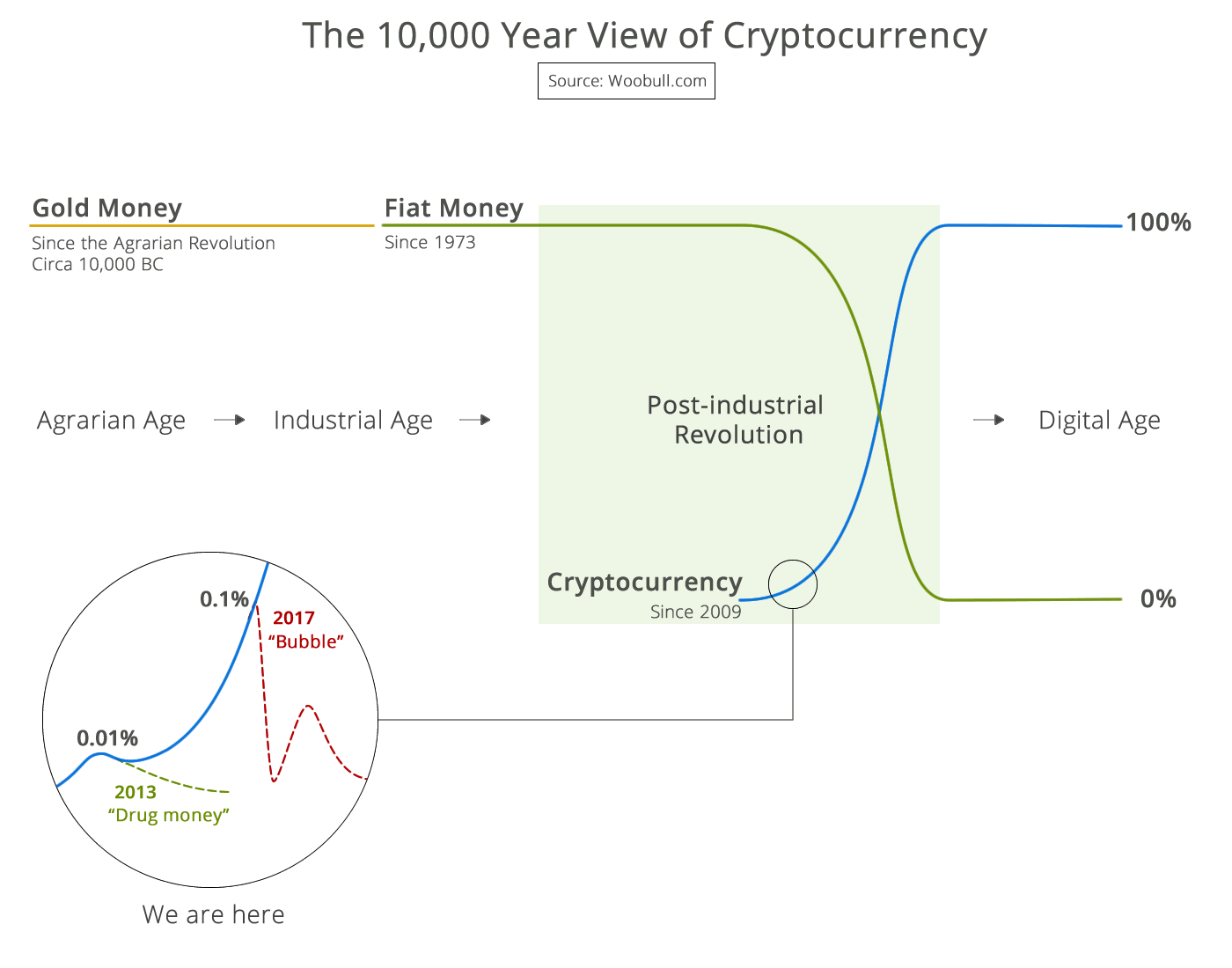 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency