I’ve been learning about One-time Pad coding. It’s kind of cool because it’s the only 100% ~theoretically~ unbreakable code. It’s not just that it’s difficult without super computers. Proof of this can be a mathematical pain, or it’s easy once you realize that any coded message is trivial to decode, but it can decode to ANY secret message. Because the bad guy doesn’t have the key, the bad guy has no way to figure out which secret message you sent. It’s not as if the bad guy can break the key to get the right message because there is an infinite supply of other possible right messages to get using other keys.
I’ve been using the easy Windows program from CNET. Download a copy and give it a try. Although it is a Windows OS program, if you are running Mac OS, you can run it using Wine and the following Apple Script:
tell application "Terminal" do script "/opt/local/bin/wine ~.wine/drive_c/Program\\ Files/CNET/otp.exe" end tell
CNET’s otp.exe program can generate keys, or you can use Linux or your Mac command line to generate really hardware random ones:
#! /bin/bash dd count=3000 bs=1 if=/dev/random of=randombytes.bin hexdump -e'"%_p"' randombytes.bin | tr -dc A-Z | head -c280 > otpkey.txt
Here’s an example where the same coded cypher message generates different secret messages:
message = SECRETMESSAGE
key = SCPQWSAVMOMVW
cyphertext = LHSIBMNAFHNCB
Notice the same ciphertext (which is what someone would intercept) can generate a totally different secret message. There are an infinite number of plaintext messages that could have been coded, based on the unknown key. Because the bad guy can’t tell which plaintext message is the one you sent, that means the code is 100% unbreakable, not just hard to break.
cyphertext = LHSIBMNAFHNCB (same as above)
key = WNKDJZIHMGGXI
secret message = OTHERMESSAGES
Here’s another interesting set to demonstrate the point that any message can be turned into any other message with a matching key:
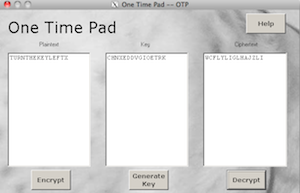
secret message = TURNTHEKEYRIGHT
key = CHNXEDDVGIIASDO
cyphertext = WCFLYLIGLHAJZLI
Try decoding the cyphertext with the “incorrect” key CHNXEDDVGIOETRK and see what you get!

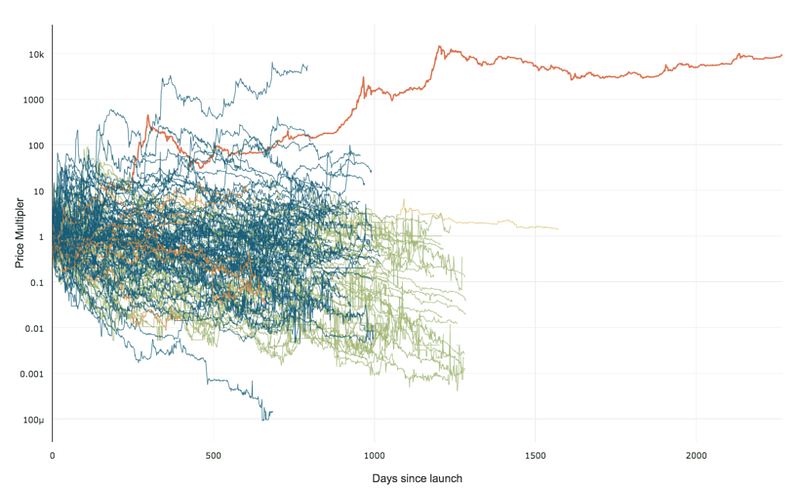 99% of ICOs Will Fail
99% of ICOs Will Fail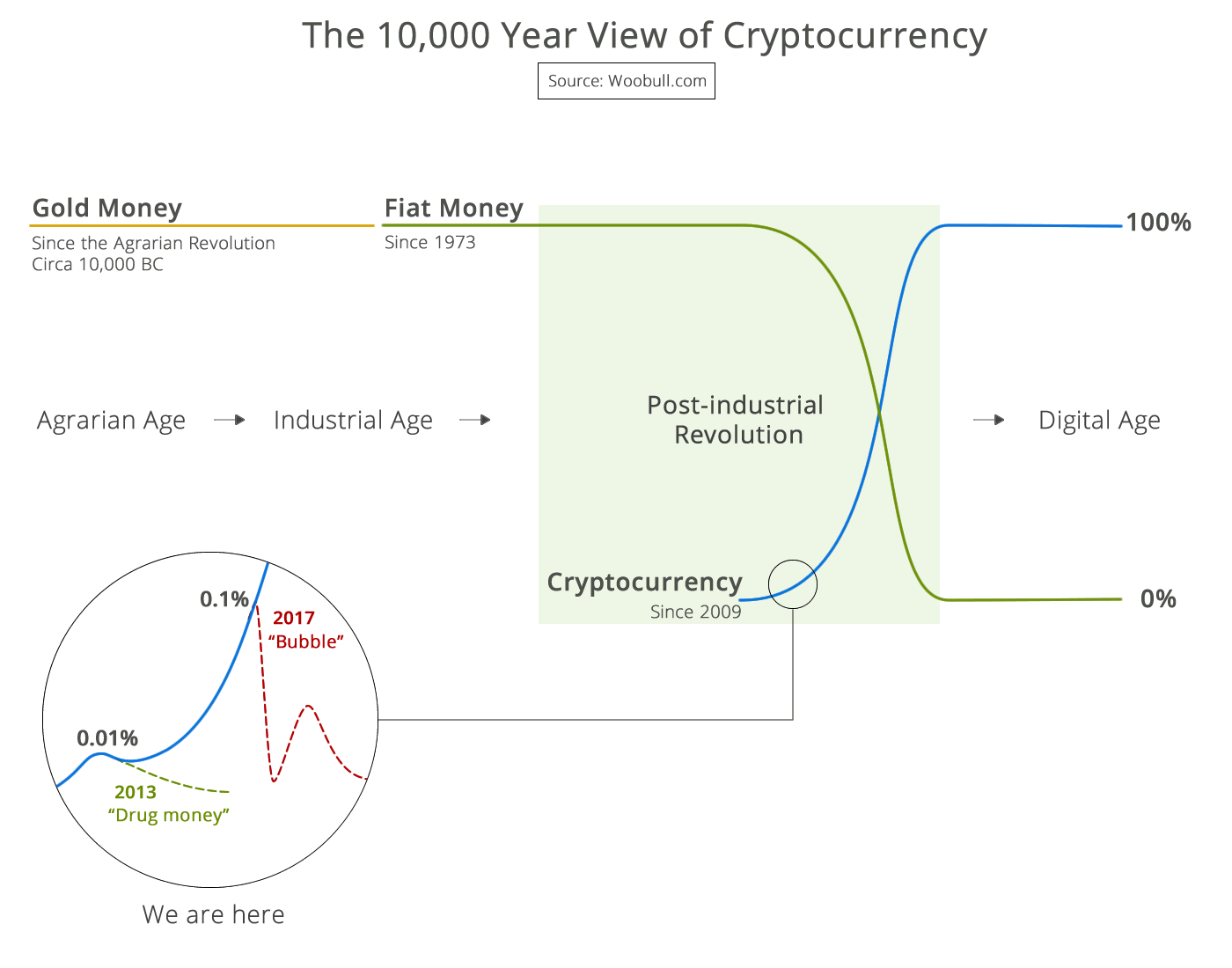 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency