One Time Pad cryptography is able to combine two items (a cyphercode text and key) to regenerate an original secret message. Visual One Time Pad techniques allow two black&white images to combine to make an original black&white secret image.
Download the program one_time_image.zip from the internet. If you’re concerned about trojans, check that you have a valid copy (md5sum 51511a8b3726c0011536ca93bd31d440). The zip file unpacks to a java program that is simple and straightforward.
It reads in an image file (B&W or color is okay) and generates two output files that are B&W, and double in size each dimension. The original image can only be reconstructed when these images are overlaid on top of each other.
Overlaying the two pictures on top of each other can best be done by printing one of the coded images onto a transparency. White areas become transparent and black areas stay black. Overlay the two, and viola! image restored. You can also do this by printing both onto white paper and holding it up to a bright light and looking through both papers. If the resolution is too high, it is difficult to hold the two images in registration compared to each other.
If you are putting cypher pictures in security boxes, or stashing them in envelopes, physical copies work best. If the resolution is low enough, you can always turn these back into electronic images with a scanner.
A quick way to view the secret image when you have electronic output files is to use computer image processing software to overlay the images. Just edit the white color to transparent on one of the images, and then overlay them in layers. Try it with the two images above, using the free program GIMP:
- Open one of the coded images with GIMP.
- Open the other image using F)ile, Op(e)n as Layers.
- C)olors, Color to (A)lpha, (be sure to select the default white color), Ok.
- Viola! You can see the secret picture.
Next up, I’m looking for a program that can let me specify two of the images and generate the third image that converts them. This is possible for text using the text coding program I posted in the prior blog entry. If I can get an image program that let’s me specify two and calculate the third, I can take a recognizable picture, and using a random-looking key-code image generated by the program, the first picture can turn into any other picture. Kind of like a digitally encrypted Dorian Gray picture!
One of the resources I enjoy is a cryptography blog by Dirk Rijmenants.



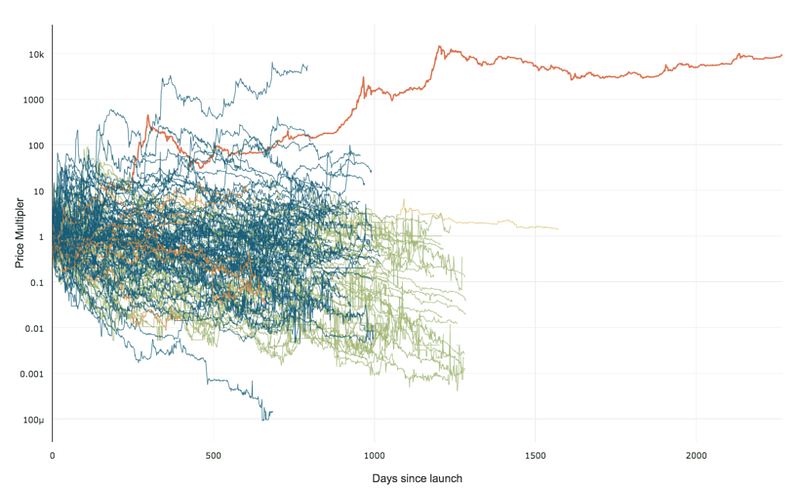 99% of ICOs Will Fail
99% of ICOs Will Fail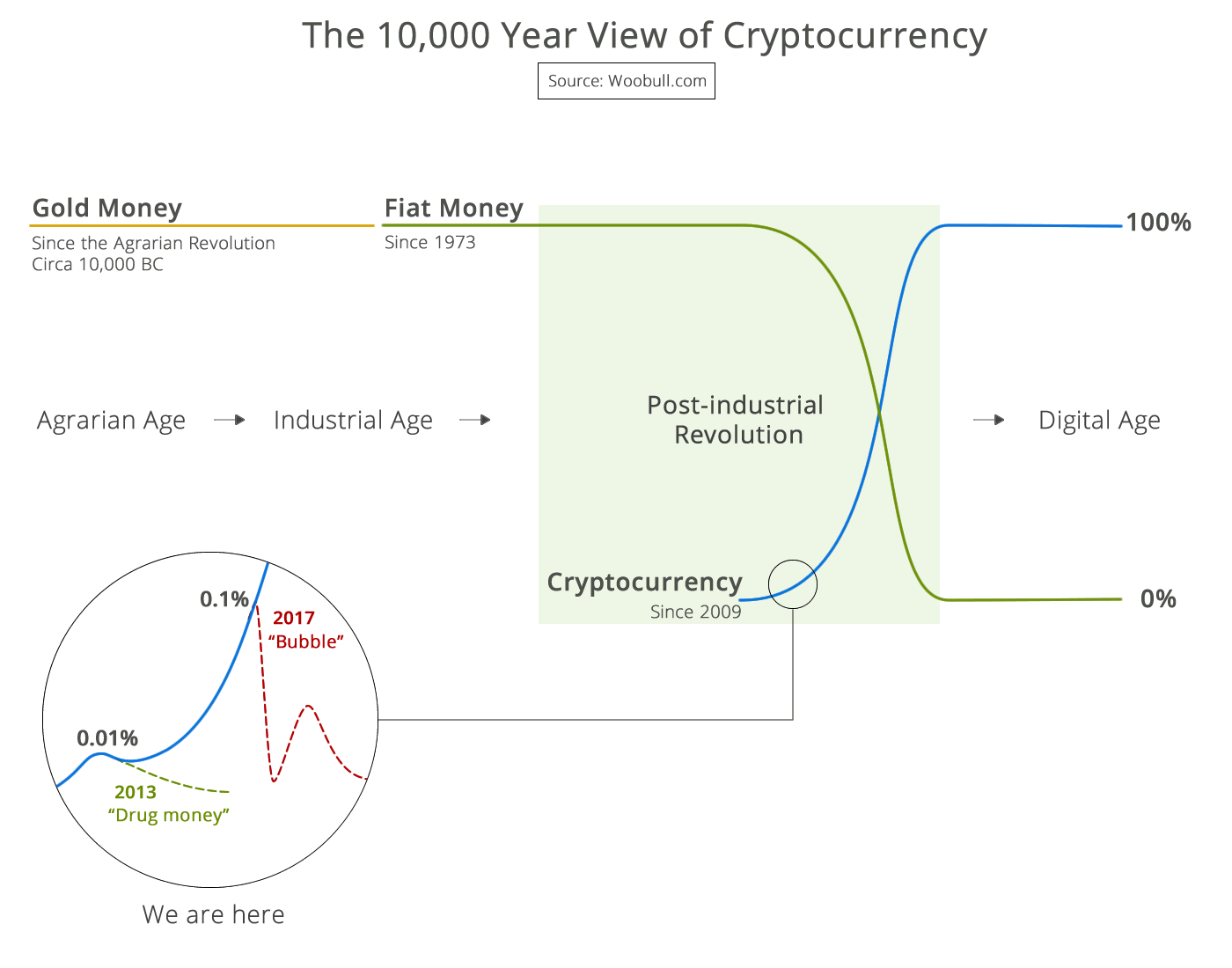 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency