The internet and information technology is accelerating the rate at which feedback loops of society stabilize on final values. The short time domain proximity of related events is highlighting a new type of phenomena. People wish to attack us, and we can stop almost anything as a nation. But doing so burdens us in ways that accomplish something equivalent to the original intended attack.
The vagueness of the issue requires a few examples. Look for the common thread running among these examples:
- Yahoo’s example of beaconing ads, shut off only by allowing cookies.
- MyPay access, where service is cut off and all notification and processes to fix the problem use the services I’ve lost.
- Telephone repair, “Call me if you have any more trouble.”
- My government IT computer, preventing hacker attacks, performs a software upgrade DoS attack at least once a week for about 1.5 hours — in order to prevent other malware from affecting my computer.
- Router based authentication where you can stop man-in-the-middle only by causing a DoS to yourself because of the huge overhead.
- We button down National travel privileges and courtesies because we need to protect from a second version of the 911 tragedy.
- Democracy works until the majority decide to vote the minority into financial servanthood.
What is the theme here? The intent of a third party is implemented by our action inflicted on ourselves. If we develop a conjugate response, tailored for the attack, it burdens us in other ways that accomplish essentially the same goal. In other words, the attacks are avoidable, but the effects of the attacks are not. We have always had asymmetric conflict, where the methods of each party are different. Attacking us in a way that causes us to finish the attack ourselves is a sub-set of asymmetric attack. They are conjugate attacks, implying that our eventual battle damage is not caused by their strength, but by our own.
There are ways to mitigate losses of conjugate attacks. [this section not yet complete]
- Keep feedback loose. Example of industrial control network through satellites. Bit flip on each end, and monitor the status. Implement half-life behavior to our “fixes”.
- Expire taxes a little bit after their purpose. New government agencies auto-expire.
- Control the PR channels. Strategic communication is your friend, to prevent other “helpful” people from boxing you in to an overreaction. Witness TSA.

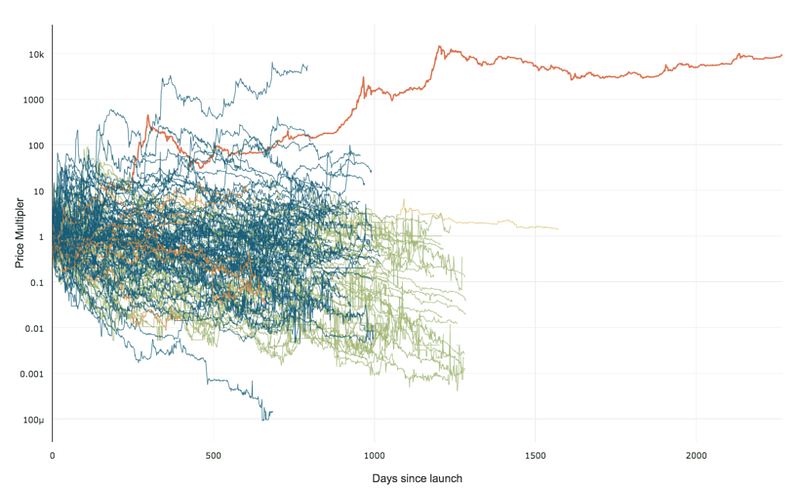 99% of ICOs Will Fail
99% of ICOs Will Fail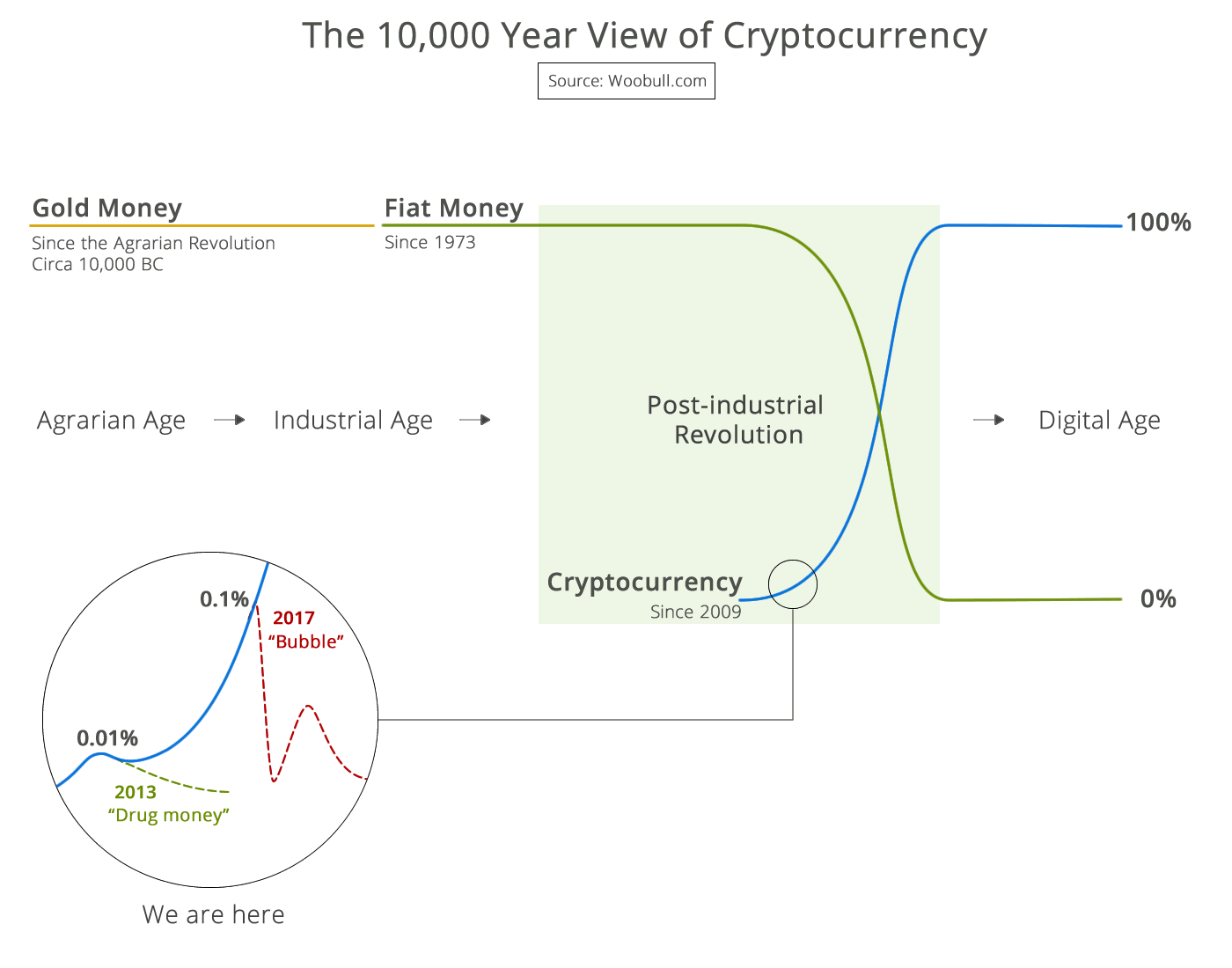 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency