Previously, I wrote about how to permanently delete magnetic data. Nobody uses removable magnetic media anymore, so I thought it’s time to outline the same procedure using internal or USB drives. A forensic posting on Code project got me started. The premise is you want to delete a file and leave no evidence that the file ever existed nor any evidence that you removed it. Here is an outline to do so.
Delete the file to the Recycle bin and empty the bin, or erase using the source application. At this stage, the original data remains on disk and file data remains in the FAT or MFT.
FULL disk erasure
If you need no data from the drive and are okay with reformatting it and maybe reinstalling an operating system, use dd to write random data throughout the entire disk. You can manually do this multiple times or write a command line script to do so, mimicking government standards for secure overwriting. Of course, this leaves a suspicion that you wiped the disk, but this can be fixed by creating a new partition table and file system and add some benign files. Or, just install a new operating system. Or, image another drive of the same size onto the target drive. The only problem will be that it will initially show no recent evidence of being used, and hence raise suspicions.
Probably the best way is to image the drive when it was new and reimage the entire image back onto your target drive. It will appear new.
If you want to keep the disk operational and just remove some files, the process is more complicated.
A la Carte step ONE
Use a wipe program to randomize all unallocated disk space. The random nature of bits will leave suspicion that you erased things. An alternate is to copy large benign files onto your disk until it errors full, then delete them. A possible benign explanation is that you collected large (legal) movie files to watch. With this story, be sure you have video player software to corroborate the story. Actually watch a few before deleting them so the execution history of the player corroborates the claim.
A la Carte step TWO
The FAT or MFT may still have evidence of old file names. To fill the unused MFT records with benign data, you need to fill the entire MFT with benign entries. Typically, 12.5% of an NTFS disk is allocated to MFT, and with 1024-byte entries, you can calculate the max number of files that can be stored. A 1 TB drive would have a 0.125 TB MFT. Divided by 1024 byte filename records yields a need for slightly less than 123 million files to fill the table. Copy more than this number of benign files to your disk and then delete them. Use files 512 bytes or less and it will be quicker because the files will be store in the MFT rather than requiring storage elsewhere on the disk.
There is no benign explanation for having done this, so it would be better to write virgin MFT entries. This could be automated with a dd command line script (determine size of MFT and write exactly that number copies of a virgin unused record), but is beyond the scope of this blog entry.
A la Carte step THREE
Erase slack space at the end of each benign file you want to remain on the disk.
Using the a la carte methods, you can prevent recovery of old data and deny knowledge that the deleted data ever existed. But you leave a trail of obfuscating behavior. Various date stamps will show that you modified the disk. Consider setting your computer clock back in time and doing all the security operations at an old date. It’s still possible to tell you did the wipe, but makes automated search and event sequencing much harder.

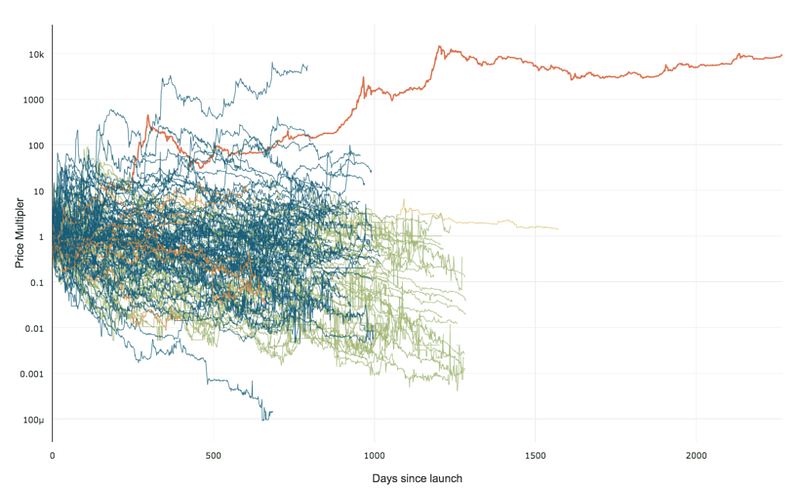 99% of ICOs Will Fail
99% of ICOs Will Fail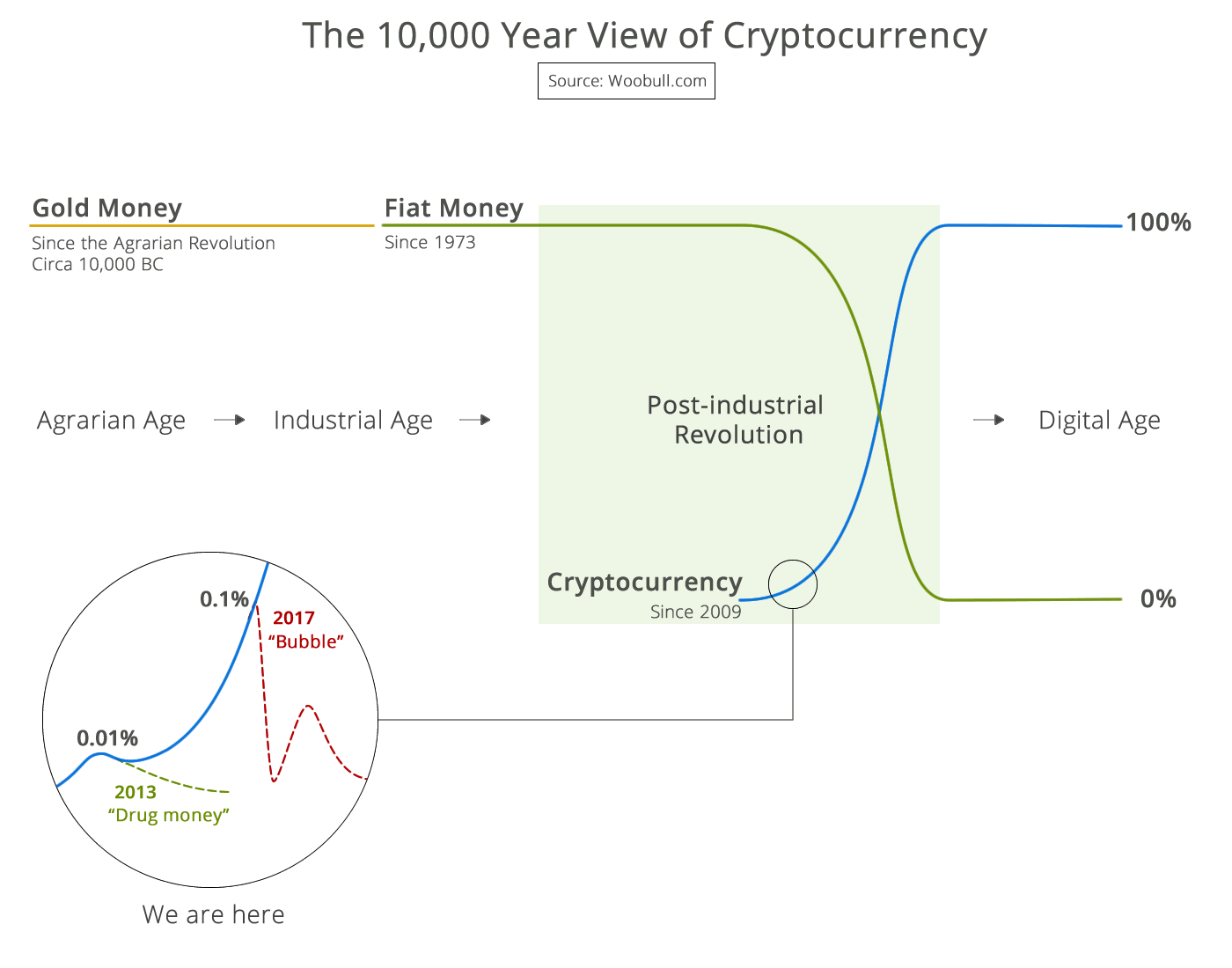 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency