The following is a slightly redacted excerpt from a research paper I completed early in 2014, introducing some implications of Big Data, or more specifically, Time Sequenced Aggregate Data. See also my blog posting about smart power meters.
…
In order to appreciate aspects of new technology, it is necessary to consider how the world of 2035-2040 will be different. Predicting the future is a gamble, but reasonable effort can outline the coarse contours. The ability to turn floods of data into knowledge will be the strategic asset of the future. Big Data infrastructure and processes will be critical.
Several recent events witness the strategic power of information and portend the future importance. The 2013 scandals surrounding the National Security Agency (NSA) collections demonstrate the value of aggregating communication message externals even when the content is not used. Note that message external data has always been available to adversaries. Stuxnet showed the physical world can be held at risk by creating false information. Google Maps offers capabilities to blue collar workers that were reserved for billion-dollar space-faring nations only a few years ago. Information will have significant strategic value. With a high degree of confidence, one can expect these trends to continue.
We will have to learn how to live in a universally translucent world where dense memory storage retains a history of everything. Already, one’s life from decades ago is available on the web, and the same will be true for each future military target. The process of detecting others or being detected will no longer be an event, but rather a process where data has to be controlled before a conflict ensues. Pre-conflict control of data will become important because knowledge will be extracted in new ways from Time-Sequenced Aggregate Data (TSAD).
Several examples of TSAD will emphasize this concept. NSA pursued their questionably broad collection without warrants because the historical (before anybody is suspect) and aggregate (everybody, not just suspects) collection must be done because only by having a large TSAD picture of normal, can they then detect when a terrorist is acting abnormally. Another example is fraud prevention detection from a credit card company, which triggers when an abnormal purchase is done; abnormal and potentially bad can be detected only because they have already tracked all the existing normal purchase behavior. Many police departments in major cities are photographing and logging every license plate that goes by just in case they want to know where you were later.
An individual example of digital stealth by controlling pre-event data would be a person changing their name to “John Smith” so that they become invisible in database searches at a later time. A TSAD operation for good is demonstrated when Google is able to aggregate search requests from thousands to report flu outbreaks before the Center for Disease Control. A demonstration from the Electronic Frontier Foundation shows how aggregate data can be used to uniquely fingerprint your computer. A government example is the desire of the National Geospatial-Intelligence Agency to map the entire globe every day even if nothing is happening because when something does happen, having the TSAD to go back and find correlated tip-off activity is important. We may have trouble remotely sensing certain bad activities, but with TSAD data, it is easy to go back and identify what the preparations looked like so we can prevent it next time. More operationally, pervasive and persistent urban area video recording has become important so that we can post-hoc go back and see when led to certain events. This is the world of TSAD and translucent data.
Future predictions of a translucent data-rich world are already creeping into the present day. Tel Aviv researchers, including one academic called, “Israel’s smartest cryptologist” have shown that 4096-bit RSA encryption keys can be broken by simply listening to the audio spectrum emitted by a computer. To do this remotely, an adversary would need a way to remotely listen to audio signals – which has been done with lasers for years.
A second contemporary example shows data aggregation is creating strategic knowledge from information crumbs. Launched in December 2013, the company Vocativ mines and aggregates data from the open web and the dark web. Behind a garish news outlet, using information shrapnel they can find from non-traditional sources, they sell knowledge and power to influence – which is where the battles of the future will be fought. Writing about aggregation of raw data to create security insights, Joel Brenner predicts, “The government becomes just another buyer of goods or services that it used to provide internally. It relies on the private sector to perform a function once thought integral to one of its agencies and exclusively within the power of the government.”
…

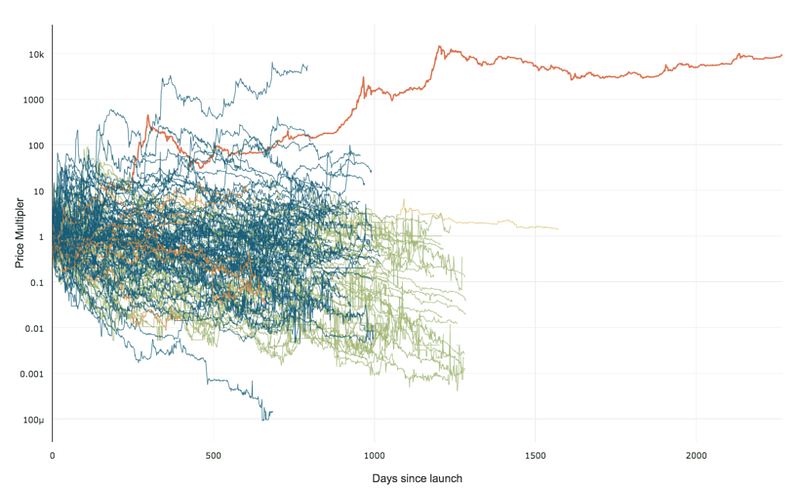 99% of ICOs Will Fail
99% of ICOs Will Fail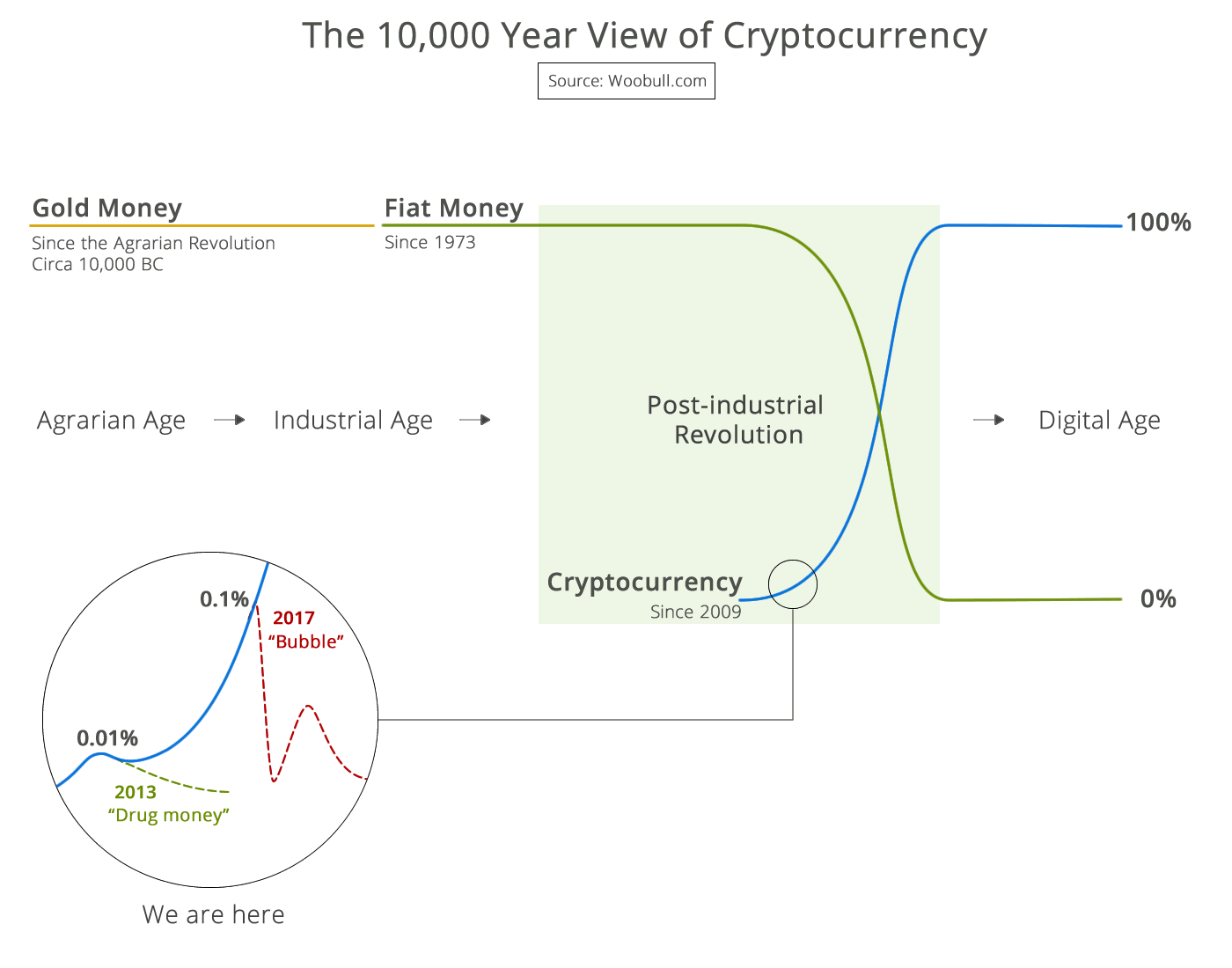 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency