I found he July 2004 USAF Science Advisory Board (SAB) report on Networking to Enable Coalition Operations. You can download a copy from the Defense Technical Information Center (DTIC), to which the SAB submits their reports. Search using the SAB Source Code 317900 to locate their reports.
On Page 9, an introduction of Data Management techniques for restricted information says,
“Information release in the network of the future should be based on the concept of metadata-derived releasability (MDR). In this approach, releasability will be determined based on the content of the information, how it is to be used, and by whom, rather than its classification level alone. Elements in the databases will have meta-tags that describe their content, based on a standardized ontology of metadata tags. Automated rule-based foreign disclosure guards are created that use these tags to determine what may be moved from national networks into the coalition network and dynamically update the coalition network as information in national networks changes. Access to information will be determined not simply by the nationality of the intended recipient, but also by the role that a participant plays and the content of the information, again using rule-based guards that examine the meta-tags to determine releasability of coalition network information to individual participants.”
MDR concerns me because it’s a paradigm shift where the data itself declares how it can be handled. Previous security classification has always been an external control on finite quantities of information (a report, or book, etc). Sure, the product has been labeled “Secret” or whatever, but this is more of a precaution for last-minute accidental exposure rather than the definition of what exposure is permissible. The Secret nature of a Secret report was known from where it’s stored, and how it’s handled, traceable back to a classification agency.
With MDR, the embedded data defines the handling procedures. Anybody who has handled an identity theft problem knows the insipid nature of this quandry. When the computer record includes faulty information, updated by some thief, no amount of arguing proves that you’re the real person and you want the information back to what it was. Think about it – How would you really, in the end game, prove that you opened the bank account rather than someone else? Same problem with MDR. How can anybody ever prove the classification authority says the handling should be different than what MDR defines? Compounding the problem is that there is no backup oversight to notice that the rule-based application programs are handling the data wrong. They’re handling it “right” as far as they’re concerned, because they’re using data in the compromised stream to define how to handle it!
If I get my bottle of white-out and cross out the word “Secret” on a report, the context of using the material still declares that it was Secret. With MDR, this is removed. A data file hack or mistake or oversight or software error immediately causes different treatment of the block of data or stream of data.

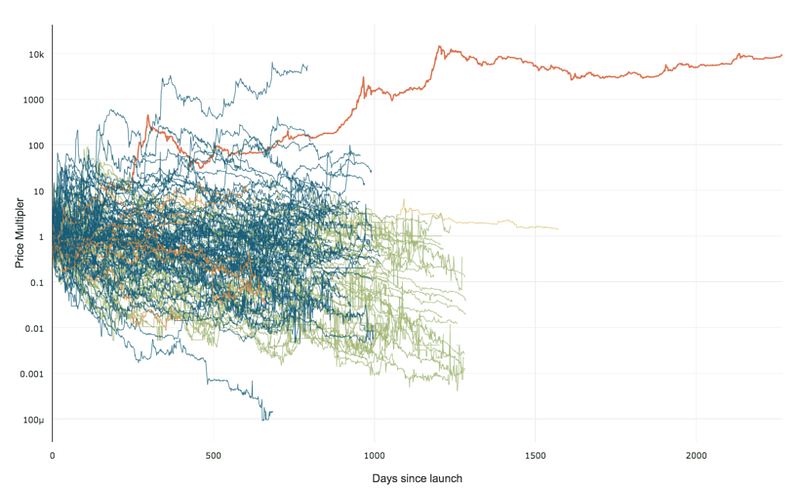 99% of ICOs Will Fail
99% of ICOs Will Fail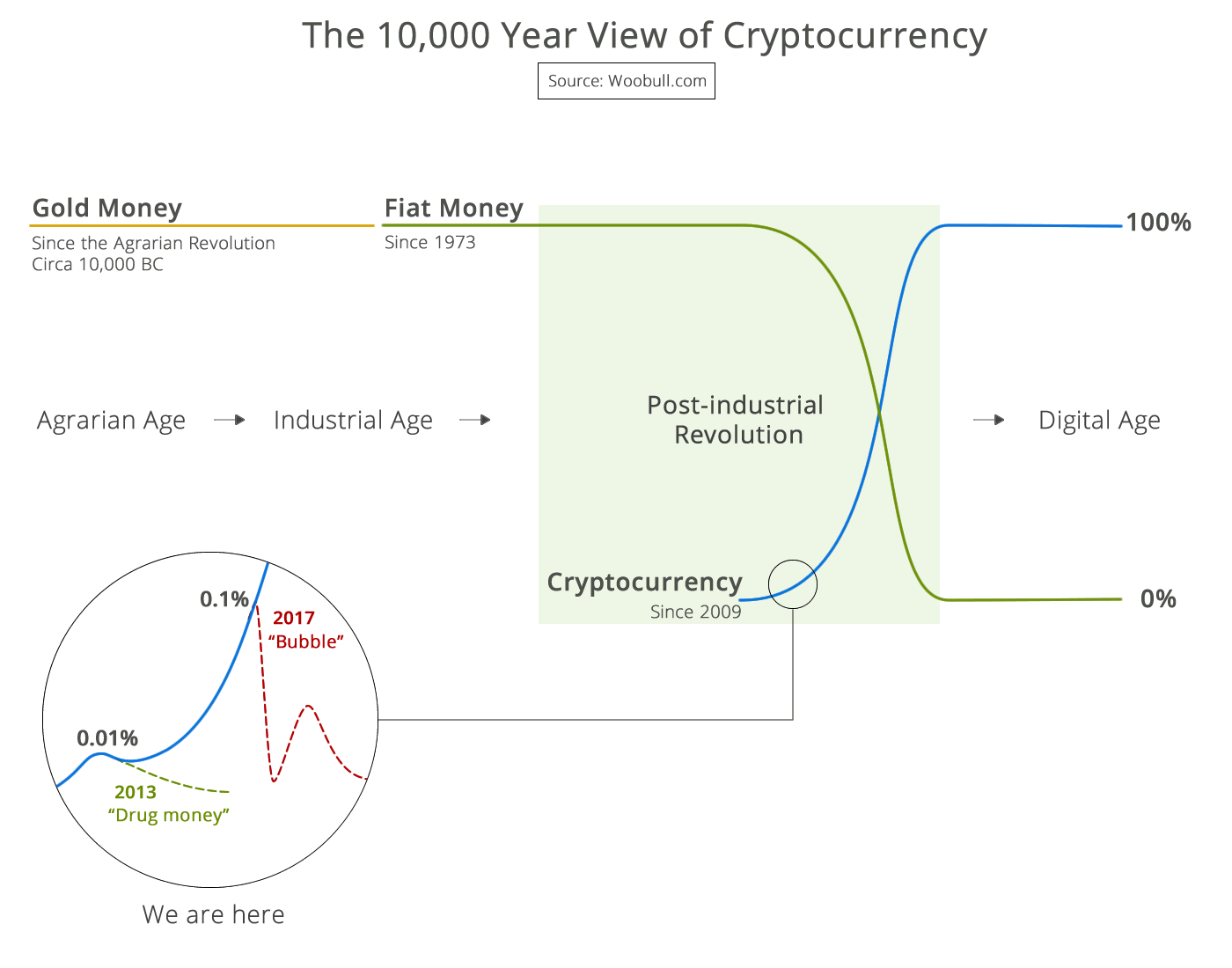 The 10,000 year view of cryptocurrency
The 10,000 year view of cryptocurrency